
The roll-out of smart meters in the UK is expected to help lower carbon emissions in homes and businesses. With the transparency and simplicity they will provide to customers with regards to both billing and understanding energy usage, it is easy to appreciate how smart meters will help the UK to lower its overall carbon emissions and meet the targets it has in place to cut these by 12.5 per cent by 2012. Prosenjit Dutta, head of advanced metering infrastructure (AMI) practice within the utilities division of Infosys and Kush Sharma, utilities lead for UK & Europe, Infosys, explainCommitment has already been shown by one of the country’s largest utility retailers, British Gas, which has plans to install smart meters in 10 millions homes by the end of 2012, and already nPower and EDF have pledged to do the same. Therefore, it is clear to see the UK is in good stead to meet its 2020 target.
However, as increased commitment is garnered and smart meters start to become a reality, consideration needs to move towards ensuring the right back-end IT processes are in place. One of the key areas which needs attention is that of ensuring privacy and security of the data stored on a smart meter and the information being transmitted across the communication network and various support systems.
With cyber attacks and data losses affecting many from an enterprise perspective, consideration into what data could and will be held on smart meters and associated enterprise IT systems about a customer will mean that energy companies will need to make sure that they have the right security controls in place to protect this information. Feedback thus far from some of our utility customers has been that they are faced with between 800-1000 attacks on their networks each month and whilst this isn’t necessarily strictly related to smart meters, it does highlight the need to ensure that security of these devices are locked in place and maintained.
The solution
So, what can be done to ensure that all this information is protected? A first step is for utility companies to ensure that a full security assessment is completed on their systems and networks to identify any potential security pain points. At the moment, there is no set way in which infrastructure security issues can be identified and anticipated, meaning that more standards are needed to protect not only customer experience, but also their personal information. With the 2020 deadline looming, the foundations need to be set sooner rather than later.
In addition, given the raft of personal information which each utility holds, any losses could have a significant impact not only on customers’ privacy, but also on the reputation of that utility. Therefore smart network security is vital to the success of their business.
Comparing and contrasting examples
Traditionally, security was a reactive task for organisations and was only considered when something went wrong. It is now clear that utilities can no longer rest on their laurels when it comes to the security and privacy capabilities of their network. Whilst smart security seems like another world for UK utilities, for those in the US, it is already a standard practice and consideration.
Alot can be learnt from American utility companies, with the most important including getting smart meter standards in place from the outset. In the US, the National Institute of Standards and Technology (an agency of the US Department of Energy) oversees not only the management of these standards, but also the development of testing, measurements, and the reference materials needed to ensure the quality of energy-related products and services whilst ensuring fairness in the market.
The good news is that we are already seeing similar steps being taken in the UK. The Government has established a central change programme – the Smart Metering Implementation Programme Prospectus. The prospectus sets out the coalition government’s programme for the introduction of smart meters which is estimated to be worth £7.2 billion. As a result, we are starting to see clients looking to become more proactive with regard to their security processes to future proof their smart meter networks. If privacy and security processes are locked in place from the outset, then this will in turn increase privacy measures to protect customers.
Securing your AMI
However, another key vulnerability for consideration by utility companies could be intrinsic to the smart meter infrastructure deployed. An advanced metering infrastructure (AMI) is widely known to be the basic building block for the smart grid enabled utility of the future; however in an AMI enabled environment, the initial and biggest challenge a utility will face is the surge of customer data and the strain on the network which could expose it to a variety of vulnerabilities.
Key vulnerabilities currently facing AMI ecosystems include:
• End point devices (Meters, Gateways and Data Collectors) – Denial of Service, Unauthorised Access to devices, Modification of Customer Data, Firmware/ Data Extraction, Circuit Analysis, etc.
• Communication Network (HAN, WAN backhaul and RF mesh) – Man in the Middle, Masquerade, Service Spoofing, Encryption Key theft, etc.
• Utilitys Datacentre (Collection engine and upstream systems) – Spurious device reprogramming and remote disconnect requests originating from Customer Information Systems.
To mitigate the risks and vulnerabilities posed by AMI adoption, it is recommended utilities engage in an upstream assessment of their existing systems and AMI impacts. This process has to be iterative and subsequently needs to be practiced even during steady state, once the AMI roll-out starts or is fully completed.
For utilities with AMI deployments in progress, or nearing completion, instead of responding to security events in a reactive mode, they should proactively pull data from smart meters at defined intervals and run correlation logics to identify and subsequently address possible vulnerabilities. Based on our observation, most utilities are currently handling AMI security threats in a reactive mode, which clearly needs to be changed.
It is therefore important utilities modify their strategy to handle threats in a proactive method by gathering near-real time information from smart meters. The adoption of proactive security practices in an AMI ecosystem should be enabled with real-time dashboards that alert systems administrators of possible attacks. This should be backed up by tools to counter such attacks. The result will be a system that is made progressively secure.
What to remember – five little things
In order to maintain privacy and security of customer data and the network, there are five key areas which utility companies must consider protecting.
The first that needs to be considered is that of electronic perimeter security. Given the range in size and scale of the communications infrastructure (which can vary depending on the size or geographic spread of your customer base), it is vital that the energy or utility company has the IT system in place to support this. In particular, a variety of wireless and terrestrial technologies pose a challenge to adopt common and more streamlined security architecture.
Secondly, by fully ensuring the security of the smart device itself, this takes into account the authentication and authorisation of a large number of end point devices such as smart meters or data collectors to the utilities network. This must consider the integration of these proprietary end point devices to enterprise standard security technologies. It is important therefore, to protect these end points from unauthorised access from wireless networks in particular.
Currently, the regulatory standards which are in place lack those of mature and established frameworks to support AMI security. As a result, many isolated and proprietary AMI standards are still being promoted by utilities as there are currently no mandated security standards for them to follow. Therefore, by ensuring that these are agreed up front allows for a clear focus for all.
As we know, sensitive customer information is stored and transmitted from smart meters. Given the recent cyber security attacks, this further shows how wireless enabled smart meters are highly vulnerable to security breaches – something which, as discussed, needs to be addressed.
Finally, the vast and often, remote number of unmanned substations pose enormous physical security challenges to any utility company. Therefore, it is important to ensure that devices, such as smart meters, can be protected from tampering.
Once each of these areas are considered, the first steps towards ensuring security controls will be in place to protect customer data on smart meters. However, if there is one thing which should be thought about over and above this, is to ensure that proactivity is maintained at all times. If we could all be a little bit more proactive when protecting customer information or fixed an issue before it became a problem, more could be done now to protect not only the company’s network, but as a result, customer information.


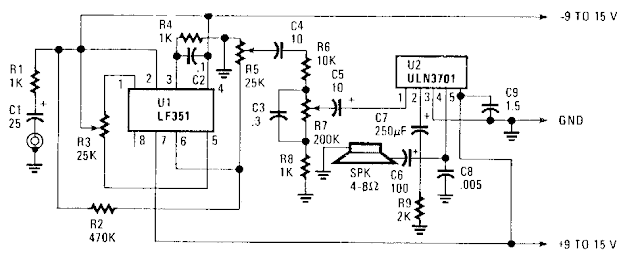






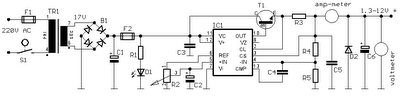









 Linear RF Power Meter Circuit Diagram
Linear RF Power Meter Circuit Diagram


